Introduction¶
The purpose of this Information Security Framework, the policies contained and the resulting procedures is to protect the customers’ and company’s interests. Therefore, our internal systems and operations, through which we handle both internal and customer information, must be secure.
The company’s approach to Information Security Management is to follow the guidance of ISO27001 which recommends an Information Security Management System (ISMS) be arranged and a process on continuous improvement be applied. This document and its subordinate parts, and importantly the actual measures taken, represent the current result of this ISMS position in terms of policy, procedures, and system.
The maturity and level of detail available within this framework reflect the efforts made thus far, which are generally a response to business, regulatory and statuary requirements and priorities. It is important to recognise that the pace of improvement and the measures taken are to be appropriate to the company’s size and to the needs of our customers.
Certus holds and manages a great deal of information, much of it personal and confidential. Information is an asset without which Certus would be unable to provide services to its customers. It is therefore essential that its information is protected from all threats, whether internal or external, deliberate or accidental, to ensure that a quality service is maintained. The purpose of information security is to enable information to be shared between those who need to use it while protecting information from unauthorised access and loss.
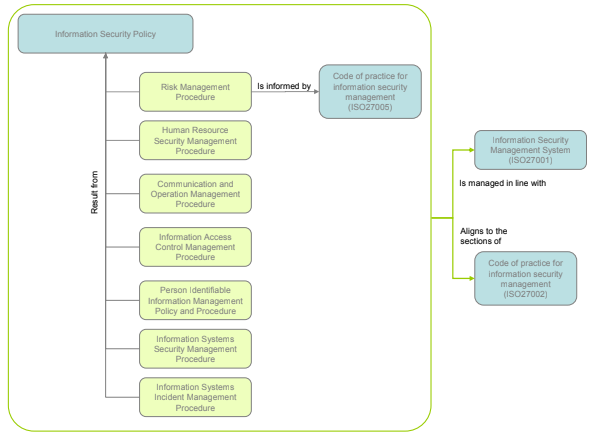
Information security is crucial in protecting that information, and it is therefore important that everyone who uses Certus’ information and information systems reads, understands and complies with the Information Security Framework. The figure below shows Certus’ general information security framework.
Figure 1: Information Security Framework